Disclaimer: this article includes links to products for sale on our store.
- Basic Layers of Online Security
- Two-Factor Authentication
- How Does Google Authenticator Work?
- Issues with Google Authenticator
- Google Authenticator Alternatives: Yubikey and Trezor Model T
- Benefits of U2F
- Drawbacks of U2F
- Trezor and Yubikey — U2F done right
- How U2F works with Trezor
- About Trezor
- Conclusion
- FAQ
In this post we are going to cover:

Plus more... Read on to learn everything you need to know about why you need to stop using Google Authenticator.
Many of us have learned the hard way that having a single password protecting our online accounts is not enough. We now use one form or another of two factor authentication. You may have even decided to use Google Authenticator to provide this second layer of protection. If you did, you need to know the risks you are taking by doing so. Thankfully there are better methods that are both safer and easier to use.
Basic Layers of Online Security
Cybercriminals are getting increasingly sophisticated, and we all must take our online security seriously to protect our ever-expanding online identity. Before we discuss Two-Factor Authentication and why you should avoid using Google Authenticator, let’s address a few other items we should have in place to protect on a more shallow level.

Strong Passwords
Advice: One of the most crucial security measures you should take is to use long, strong, unique passwords for each site. Admittedly, that can be cumbersome. However, since weak or stolen passwords are responsible for more than 80% of hacking-related security breaches, secure passwords are a must.
Fortunately, the LastPass Password Generator simplifies the creation and maintenance of strong passwords. This password generator tool creates complex, nearly-impossible-to-crack passwords consisting of multiple numbers, letters, and symbols. LastPass generates different passwords for each app or website, and it runs locally on your Windows, Mac, or Linus computer or your iOS or Android device. The passwords the tool creates are not sent across the web.
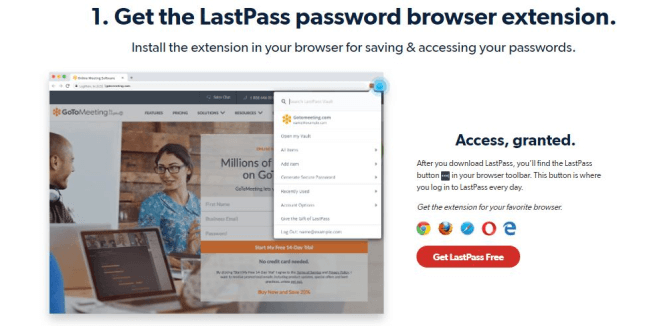
Anti-Virus and Malware Protection Software
Advice: Once you've dealt with your passwords, you need to secure your computer and mobile devices. Although your computer may have built-in virus and malware protection, it's best to install your own.
There are several widely regarded cybersecurity solutions available, including Malwarebytes and Bitdefender. Those programs have free versions, but tighten up your security by making the minor investment in the paid versions.
Now let’s get back to Google Authenticator and Two-factor authentication.
Two-Factor Authentication
Info: Two-Factor Authentication - also known as 2FA - is like a second password on your online accounts.
Two-Factor Authentication - also known as 2FA - is like a second password on your online accounts.
Without 2FA, you simply enter your username and password, and the website or app grants you entrance. The password is your single authentication factor.

2FA adds an extra step to your log-in process. It requires you to have two out of three types of credentials before letting you into your account. Those types of credentials are:
- something you have, such as an ATM card, a phone, or a fob
- something you know, such as a pattern or personal identification number (PIN)
- something you are, such as a biometric like a fingerprint
There are two main types of 2FA. The most common type, the Time-based One-time Password (TOTP), is epitomized by Google Authenticator, the grandfather of all 2FA apps. The other type, which will be discussed later in the article, is Universal Second Factor (U2F).
And…there are two kinds of one-time-passwords:
- SMS one-time-passwords
- App generated one-time-passwords
Warning: SMS one-time passwords are widely known to be unreliable. Just ask anyone who has ever been the victim of a sim-swapping attack.
Certainly, time based one time password apps like Google Authenticator are far more secure than SMS.
How Does Google Authenticator Work?
Authenticator apps work much the same way as SMS 2FA does, but use an app on your phone to send you the code instead of sending over a text message. This means that the code cannot be intercepted remotely by hackign your sim card. The hacker would need your physical phone to get the code.
Google Authenticator verifies that you are who you say you are based on a secret you and the provider share online. When you log into a website, your device generates a code based on the current time and the shared secret. To complete your website login, you must enter this code manually on the site before it expires..
So how does the server know how to let you in? It generates the same code you have so it can cross-check your code. Since both you and the site you’re trying to log on to possess the secret and make the request at the same time (that is, you use the same input factors), you’ll both generate the same hash.
Issues with Google Authenticator
Info: Google Authenticator is easy to use, which is a welcome attribute in the often-convoluted cryptocurrency world. However, this old app—it was released in 2010—does have some security vulnerabilities and inconveniences.
First, you have to manually input the code at logging in, adding another step to the log-in process. You’ll also have to take extra steps to back up the secret. But services often offer reserve codes instead of requiring you to save the secret. If you log in with one of those codes, you’ll have to go through the whole registration process all over again.
Those backup codes are sent online, which is one fundamental security weakness. If hackers gain access to a company’s passwords and the secrets database, they can access every account. Unfortunately, there’s no shortage of stories about websites and even reputable cryptocurrency exchanges that have been hacked.

Another unsecure area is the secret itself, which shows up as plaintext or QR code, not as a hash or with a cryptographic salt. Therefore, the company’s servers probably store the secret in plaintext form. Since the provider has to give you a generated secret during registration, the secret can be exposed at that time.
Warning: The primary concern with using a Time-based One-time Password like the Google Authenticator is that you have to trust the providers with protecting your secret. But can you, or should you, trust a provider?
Google Authenticator Alternatives: Yubikey and Trezor Model T
The second type of Two-Factor Authentication: Universal Second Factor (U2F)
Info: The most popular type of 2FA is the Time-based One-Time Password. But the second, albeit the less-popular type of 2FA, Universal Second Factor, is undoubtedly more secure.
The Universal Second Factor is a universal standard for creating physical authentication tokens that can work with any service. U2F was created by tech giants, including Google and Microsoft, to address the vulnerabilities of TOPT. It’s somewhat ironic that Google did not retire its old app, the Google Authenticator, after helping create U2F.

If you’ve heard of Yubikey—a physical USB key that allows you to log in to LastPass, the password generator tool discussed at the beginning of the article, as well as some other services—you’ll grasp the concept of U2F. However, unlike standard Yubikey devices, U2F is a universal standard.
Advice: At any rate, here's the critical difference between TOPT and U2F: to verify your identity, U2F uses public-key cryptography. Therefore, unlike TOPT, nobody else knows your secret. You hold the private key, which means you (and only you) can gain access to your account so long as you are the one holding the physical device.
With U2F, the server sends a challenge, and your private key (the secret) signs it. The server can verify the message by using the public key in its database.
Benefits of U2F
There are many benefits to using U2F. Here are a few:
- Privacy: With U2F, your private key will never be sent into cyberspace, allowing you to enjoy one of most coveted statuses on the web: actual privacy. Thanks to public-key cryptography, you won’t have to worry about sharing any of your confidential information.

- Iron-clad security: 2FA using public key cryptography protects against session hijacking, phishing, and various types of malware. Since U2F doesn’t rely on a shared secret stored on a provider’s database, an attacker cannot steal a whole database to access a user’s account. Instead, he’ll have to go through the time-consuming, costly route of targeting an individual user and stealing their hardware in person.
- Easy to use: U2F devices work right out of the box thanks to support through universally available browsers and platforms; there are no codes to type or drivers to install.

- Cost-effective: Customers can choose from a variety of devices at different price points, all of which are surprisingly affordable, given their cutting-edge technology.

Drawbacks of U2F
The chief advantage of U2F is also its major drawback. With U2F, you can often back up your secret, otherwise known as your private key. That means you are responsible for your own security. If you lose the private key, nobody can recover it for you. However, you also need not trust any company to protect your private key.
Info: Another drawback to U2F is that backup is not always an option. For example, there's no way to back up the hardware-based authentication solution Yubikey.
Trezor and Yubikey — U2F done right
Fortunately, there’s a way to enjoy the gain of U2F without the pain by using Trezor. Trezor was initially created to store private keys and serve as an isolated computing environment. Although it still performs admirably in its original role as a secure Bitcoin hardware wallet, Trezor can now be used in more ways thanks to widely applicable private/ public key (asymmetric) cryptography.
Chief among these expanded uses is Trezor’s function as a hardware security token for U2F. Unlike other U2F products, though, Trezor offers backup and recovery functions as well as convenience.
How U2F works with Trezor
When you log into a website, you usually initiate the authentication process with your user name and password. You’ll follow that procedure with Trezor and U2F, but after that, you’ll take another easy, painless step: you’ll confirm your login by clicking on your Trezor device.
Info: Unlike other tokens, Trezor and Yubikey use unique signatures for all registered user accounts. Also, backing up and recovering the Trezor and Yubikey is stress-free.
When you initially set up your Trezor device, you will back up your recovery seed. This seed represents all the secrets/private keys the Trezor generates, and it can be used to restore your hardware wallet at any time. Backing up the recovery seed is a one-time process, and it saves an unlimited number of U2F identities.
Your seed is stored securely in the Trezor. Since it never leaves the device, your private key is immune to viruses and hackers.
Trezor also offers phishing protection with on-screen verification. As cybercriminals continue to become more sophisticated, the phishing websites they put up closely resemble original sites. By always displaying the URL of the website you are logging into, and letting you know exactly what you are about to authorize, Trezor protects you from phishing attempts. You can verify that what was sent into the device is what you expected.

You can order your Trezor One here or Trezor Model T here.
About Trezor
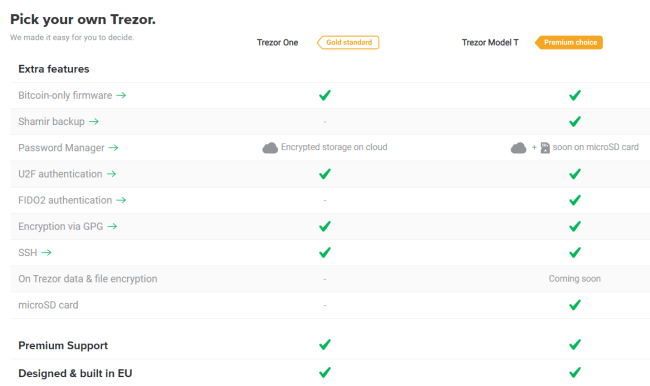
Created by SatoshiLabs in 2014, the beginner-friendly Trezor One is the gold standard of hardware wallets. It offers unparalleled security for cryptocurrencies and password management and serves as the second factor in Two-Factor Authentication. These features combine with a user-friendly interface that even novices can navigate with ease. Passphrase entry and device recovery are available securely via a computer or modem.
The premium Trezor Model T is the next-generation hardware wallet. Like the Trezor One, the Model T is appropriate for novices and sophisticated investors alike. It retains the benefits of the Trezor One but offers a sleeker, more intuitive interface for improved user experience and security. It features a touchscreen, faster processor, and advanced coin support. Passphrase entry and device recovery are available directly on your Trezor Model T.
COMPARISON
Conclusion
For cryptocurrency investors, security is a paramount concern. There’s no point in investing time and money in learning about crypto and growing your crypto portfolio unless you secure those assets. The rewards of cryptocurrency are great, but so are the risks.
If you haven’t done so already, plug security leaks such as weak passwords and unprotected computers and mobile phones. After addressing those issues, you may want to consider using Two-Factor Authentication (2FA). Although it’s tempting to use free, widely available methods such as Google Authenticator to secure your cryptocurrency assets, Authenticator has its vulnerabilities and inconveniences.
The second type of 2FA, Universal Second Factor (U2F), is more secure than Google Authenticator. A secure hardware security token for Universal Second Factor, Trezor, offers far more features and security than Authenticator. In the crypto world, it’s all about security. Remember: you are your own bank!
Since you, as a crypto investor, assume more responsibility for security than a traditional investor, invest in the best security solution. Secure for yourself either a Trezor One or a Trezor Model T today.
FAQ
What is the use of a YubiKey?
A Yubikey is used to authenticate web logins. It can be plugged into computer or phone.
What is LastPass used for?
LastPass is a password manager that stores all your passwords in one place. This is called a Vault through which LastPass remembers your password for you.
Why is SMS two-factor dangerous?
SMS two-factor is dangerous because it is easy for hackers to hijack your text messages via ‘SIM swapping’.
What if my password manager gets hacked?
If hackers get all the data the password manager has, they’d still have to try every possible password for your data to see if it works, since the hackers see only a bunch of scrambled passwords.
Is Trezor Model T safe?
If a very motivated and highly skilled attacker were to physically get hold of your Trezor Model T, your coins may not be safe. However, this attack has never been performed outside of a laboratory, so the threat is remote. In almost all cases, a Trezor Model T will keep your coins very safe.
Which is better - Trezor or Ledger?
Ledger is more secure if your wallet is found, however the Trezor does not have Bluetooth, which reduces the risk of a remote attack on your device. The Trezor also has more features and a better screen if you do with the Model T.






