Disclaimer: this article includes links to products for sale on our store.
- Improving Trezor Privacy with Tor, VPNs, Wasabi, Electrum and Full Nodes
- Hide Your IP Address and Store the Public Key on Your Computer
- 1. Run Trezor with Tor
- 2. Run Trezor on Electrum Wallet
- 3. Run Trezor on Wasabi Wallet
- FAQ
In this post we are going to cover:

Plus more... Read on to learn everything you need to know about how to improve Trezor privacy.
Improving Trezor Privacy with Tor, VPNs, Wasabi, Electrum and Full Nodes
Trezor’s web wallet provides one of the simplest ways to manage your bitcoins. It’s a straight-forward point and click experience which easily gets the job done. If you’re a newbie, then it’s a great option to start your journey of Bitcoin financial sovereignty.

But when you’re a more advanced user, you should also consider privacy as a criterion for security. And most of the times user friendliness comes with tradeoffs. In the case of Trezor, using the hardware wallet via wallet.trezor.io sends some data to the manufacturer. The two attack vectors involved are:
1. Your IP address;
2. Your extended public key (xpub).
The IP address reveals your location (country and ISP). On the other hand, the xpub stores all the Bitcoin addresses you generate. It’s an extended public key which gives full nodes access to data on how many coins you store in the wallet.

If you run and use your own full validating node, you store the xpub on your own device. But if you connect to the Trezor wallet, you use their nodes.
And while this data may be worthless for Trezor, hackers will find a lot of value in it. Bad actors who steal the information will definitely try to link IP addresses to funds.
COMPARISON
Hide Your IP Address and Store the Public Key on Your Computer
Unless you use VPN and/or Tor, you expose your IP address and location to every website you visit. And if a hacker finds your internet provider, then be wary of social engineering attacks.

How can they find out where you live? They may call your ISP to ask for maintenance services at your house. And if the phone operator is nice, the hacker will also inquire for an address confirmation.
Warning: But if you are a known bitcoiner who posts a lot on social media, there are other attack vectors. If you post pictures of your neighborhood and whereabouts, you're even more exposed. The IP address would only work as a confirmation that you have terrible opsec.
Now let’s talk about why public key security is important. A hacker who accesses Trezor’s xpubs will be able to identify which wallets store most BTC. You may think that this doesn’t matter because they still don’t have the private key to spend your coins. While this is true, there are other ways to steal your bitcoins.
After associating IP address with wallets, it’s time to determine the cost of attack. Criminals will ask themselves “how much does it cost to extort the coins from this person?”. If you own large amounts, they can afford to take more risks. And if law enforcement in your area is terrible, you’re more exposed. There are lots of factors to take into account.

Yet if you own small amounts, it’s likely that the cost of attack exceeds the benefits. This means that you are far less likely to deal with criminals trying to steal your bitcoins. So this is an extra reason to not hold too many bitcoins in one single wallet.
If you live too far away, the hackers may also sell the data on dark markets. There are plenty of criminals who are proficient in physical theft. And if all the incentives align, they can attempt a $5 wrench attack.
But then again, what if you don’t have to reveal any of this information with Trezor? And what if you don’t share it with any company and manage it yourself?
Here at Privacy Pros we enjoy teaching you how to minimize the amount of data you share. Privacy is the mother of good security, and if you own bitcoins you should always be wary of it.
This article includes 3 of the best ways to improve your privacy while using Trezor hardware wallets.
1. Run Trezor with Tor
The Tor browser is the best free privacy tool. It’s an open-source project that you use to hide your IP address.
By using Tor, you break any associations between your location and your Trezor xpub. Whoever hacks the Trezor database will only see the IP address of the Tor relay node. And if the encryption gets broken for that Tor relay node, there is another one that covers it. This means that you’re very much protected against doxing.
Trezor’s online wallet is compatible with the Chrome, Firefox, and Brave browsers. And since Tor uses code from Firefox, they’re very similar in design and architecture. To boost your privacy, Trezor themselves have created a way to use their wallet via Tor.
Advice: Before you start, make sure you download the latest version of the Tor browser. It will help you avoid bugs and grant you the greatest amount of privacy.
This next section explains the process of configuring Tor to work with your Trezor hardware wallet. Keep in mind that the experience is the same on every operating system. So it doesn’t matter if you’re on Windows, Linux, or Mac. Tor is the same all across the board.
After you install Tor, open a new window and type “about:config” in the address bar. A warning which reads “Proceed with Caution!” appears on the screen to explain that making changes can compromise anonimity. But our goal is to only make the Tor browser communicate with Trezor Bridge. And for this purpose, we are only adding one exception.
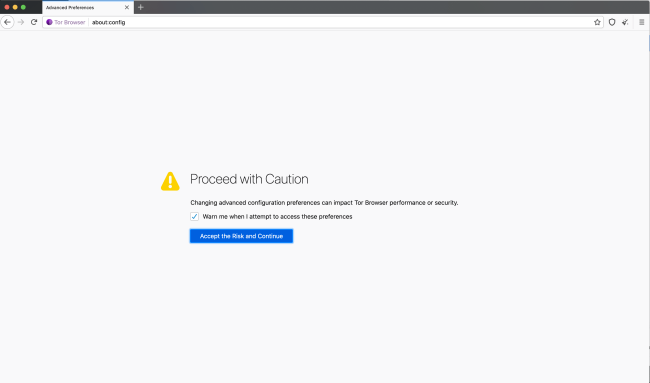
So click “I accept the risk!” and a list of preferences will appear. These are the settings that keep your browsing private and secure. So in the search bar, type “network.proxy.no_proxies_on”. Once the inquired value appears, double click it and set its new value to 127.0.0.1:21325.
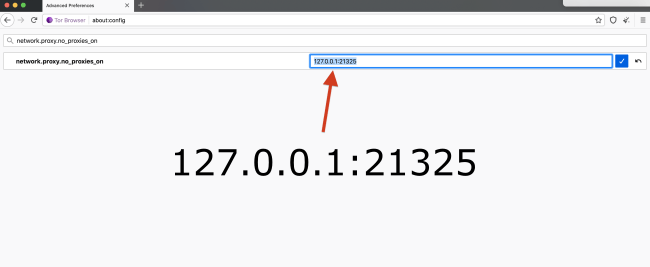
After you type in this address, click “OK” and you’re all set. Restart Tor, generate a new circuit, and then visit wallet.trezor.io. You will see that your Trezor hardware wallet now works with Tor.
Now your privacy and anonimity got a boost. So as long as you access the web wallet using the Tor browser, it’s impossible to link your public key to your real IP address.
2. Run Trezor on Electrum Wallet
Electrum is one of the most popular and feature-packed Bitcoin wallets. It’s the top choice for people who do multisig setups. And when it comes to hardware wallets, it’s likewise excellent.
With Electrum, managing your Trezor is an intuitive point-and-click experience. And if you use it to create a new wallet, your xpub gets stored and encrypted on your hard drive. This way, Trezor will not have access to your public key.
Electrum connects to random full nodes from across the Bitcoin network. This means that there is an element of unpredictability in each session. It’s very unlikely that you share your IP address and xpub activity with the same node twice. For your IP address, you can use a VPN service or even route Electrum through Tor.
To activate Tor routing, click the “Network” button in the bottom right corner of the window. Then go to the “Proxy” tab and tick the “Use Tor proxy at port 9150” box. Save the settings and restart Electrum wallet. Now you should use the service with greater privacy, thanks to its native Tor routing.
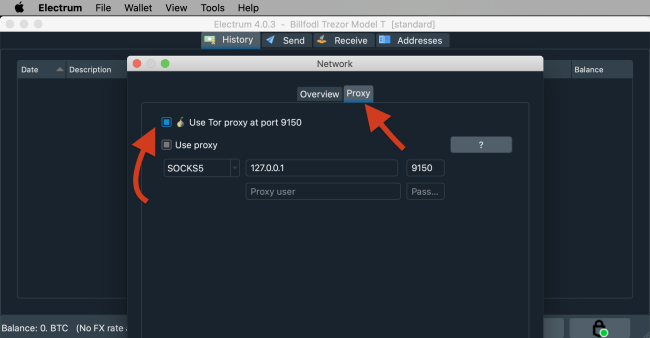
Now that you’ve maximized your privacy, it’s time to set up a new wallet with your Trezor. And yes, you can also import an existing one. But if you’ve previously shared your xpub, it’s better to do a new setup. Remember: the purpose of this guide is to empower you with the greatest degree of privacy.
Info: In the first screen, Electrum will ask you to name your wallet. The default format is "wallet_number", but you can choose any name you want. This doesn't affect the key generation process, but exists for labelling purposes. It's always good to know the purpose of each wallet you create.
After choosing a name, click “Next”. This next screen is the most important, as you pick the type of wallet you want to create. In our case, we’ll choose the Standard wallet. But if you want to create a multisig or import private keys, you also have dedicated options.
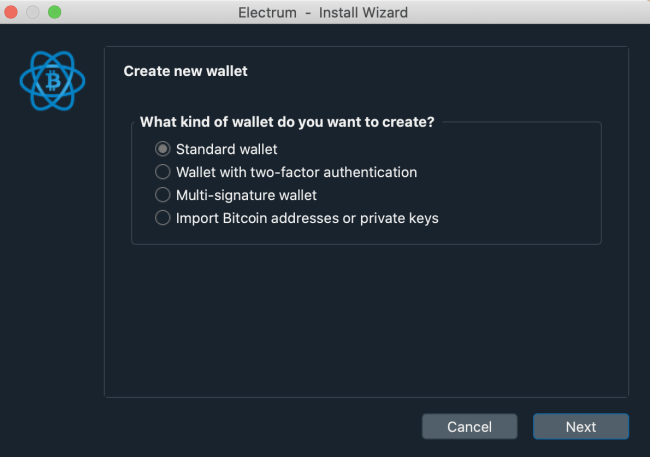
Since we’re using a Trezor for this process, we’re going to pick “Use a hardware device”. Before proceeding, make sure to connect your Trezor to the computer. If you set a PIN, you will have to enter it before proceeding. New Trezors should get detected as “An unnamed trezor”.
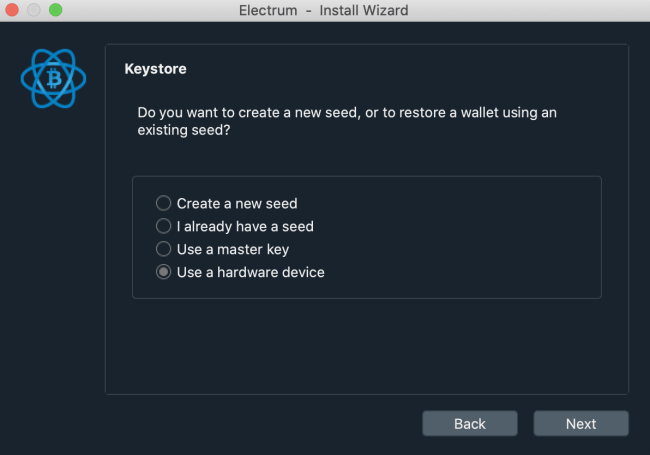
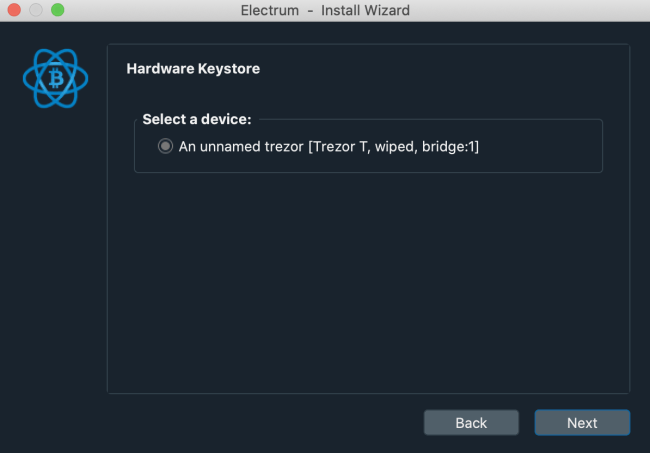
The next step of the initialization involves another important choice. And since we’re creating a new wallet with Electrum, you will choose “Let the device generate a completely new seed randomly”.
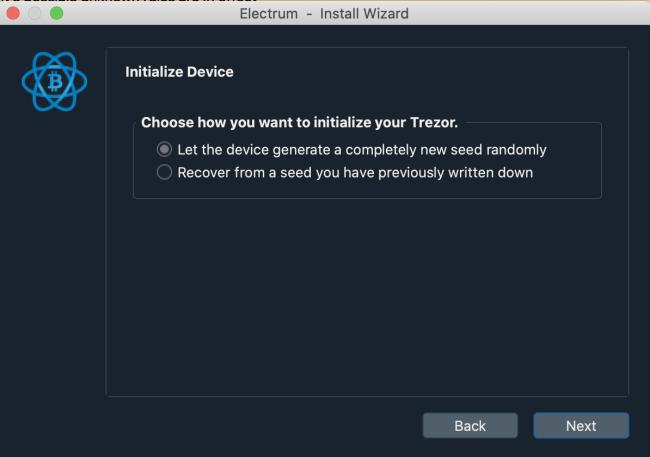
This next window offers you all the interesting setup options. On a Trezor Model T, you will be able to do a single seed BIP 39 setup, a Shamir backup (20 words per share) or even a Super Shamir (33 words per share). On a Trezor One, you only have the single seed setup with 12, 18, or 24 words.
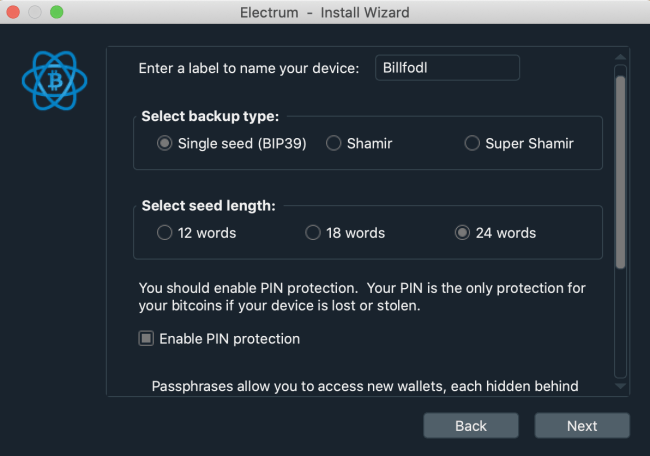
For simplicity purposes, a single seed wallet with 24 seed words is more than enough. But if you need something more sophisticated, consider the Shamir backup. This is also the part where you can name your hardware wallet. Once again, this is only done for labelling purposes and has no impact on security.
Advice: It's worth pointing out that the default setup on the Trezor web wallet creates 12-word BIP 39 wallets. In this regard, Electrum gives you much more flexibility and security options. More words are harder to hack. But if you count on memorization it's better to choose simplicity.
After you click “Next”, you’re going to have to choose if you want to use a passphrase. From a security point of view, it’s recommended to use this passphrase. It will make your device inaccessible without this password. Also, it’s always better to enter this word on your device, as opposed to typing it on your computer. Your computer may have key-loggers, but the Trezor is safer.
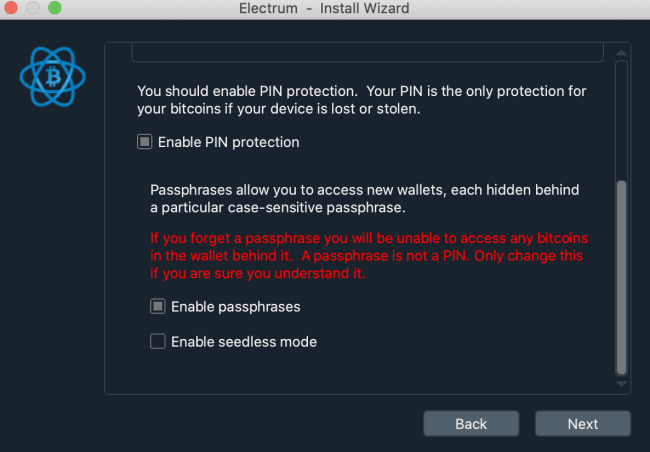

You can also enable seedless mode, but it’s far less secure and relies on digital backups. So it’s better to grab a pen and a piece of paper to write down your words. And if this wallet is important to you, you should also get a Billfodl to secure it with steel.
Info: In the next section you will have to grab your Trezor and write down your BIP 39 seed words. The instructions presented are for the Model T, but the Trezor One works the same way.
On the screen of your hardware wallet you will first have to agree with the Terms of Service. This legal document is more of a disclaimer which makes you responsible in the event of losing funds.
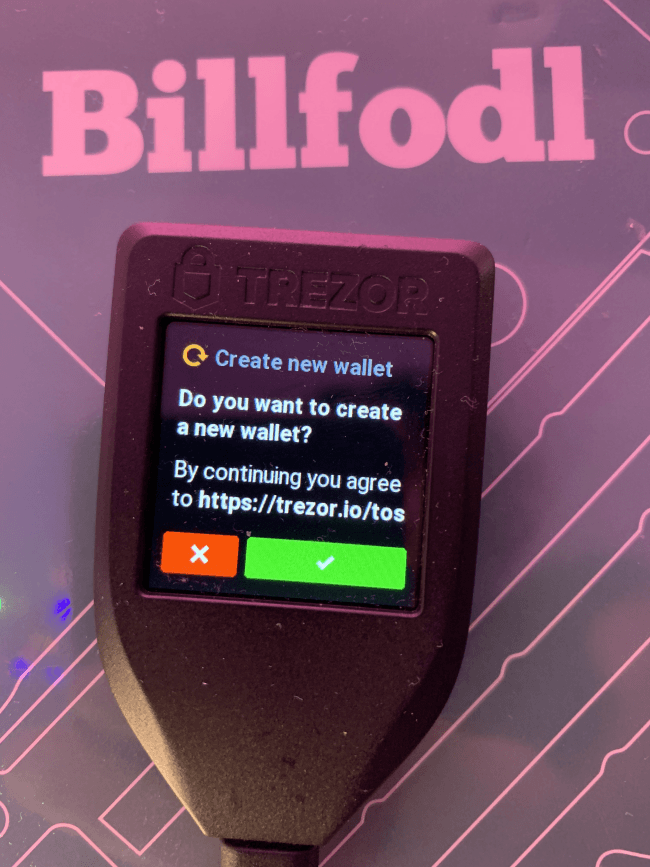
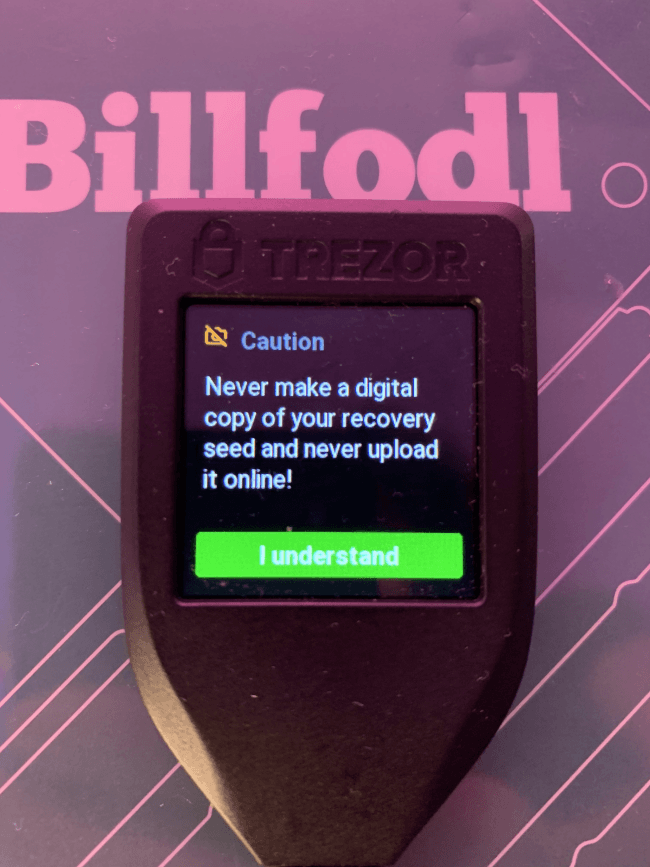
Then, if you set a PIN for your device, you will have to enter it. The next screen greets you with the message “New Wallet Created Successfully!”. But to save your 24 words, you will have to press the “Back Up” button. And before you get to write the words, Trezor warns you against making digital copies. It’s better to keep everything offline.
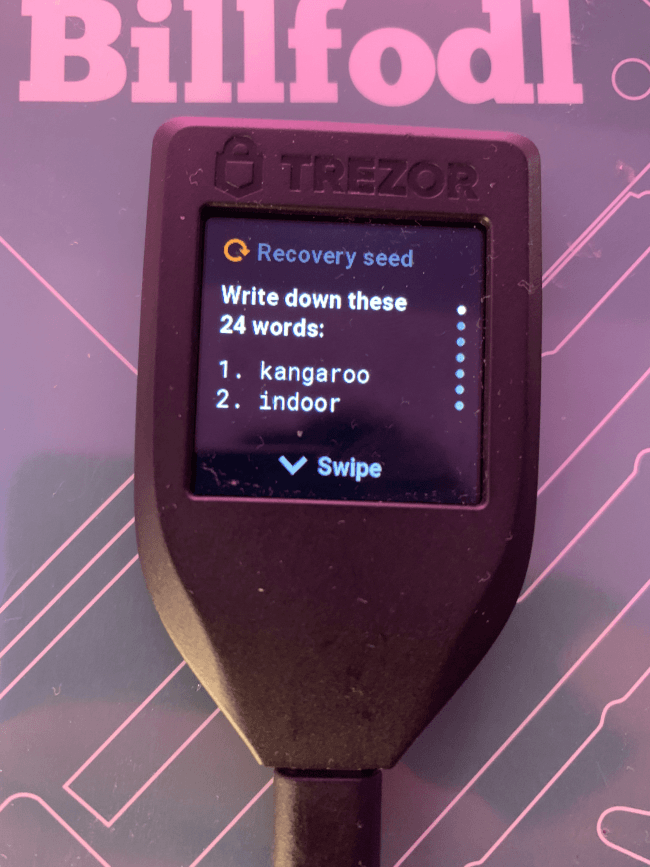
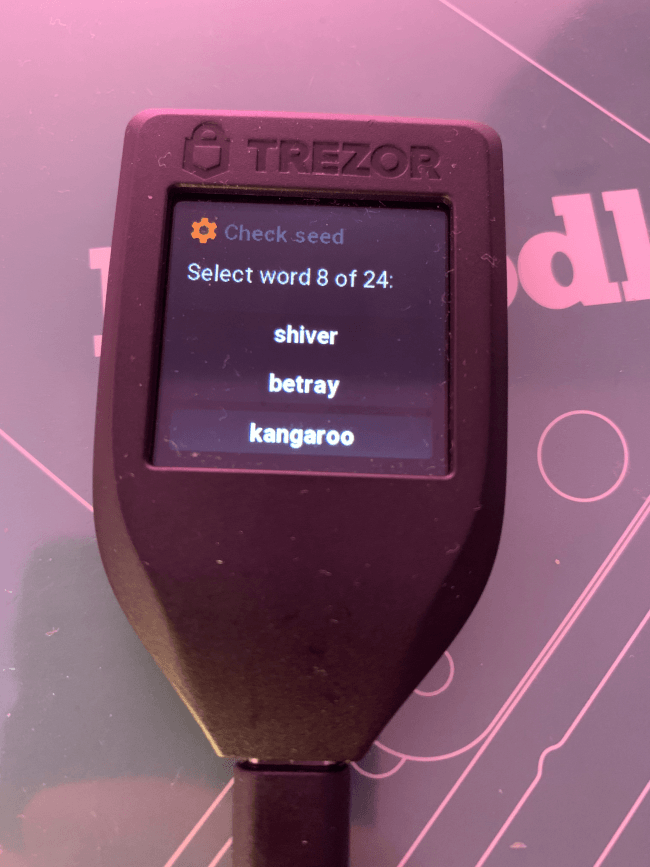
Then you will have to write down the 24 words that get displayed on screen. To make sure that you aren’t making any mistakes, Trezor will make you verify 3 random words. And after this, the message “You have finished verifying your recovery seed” will greet you.
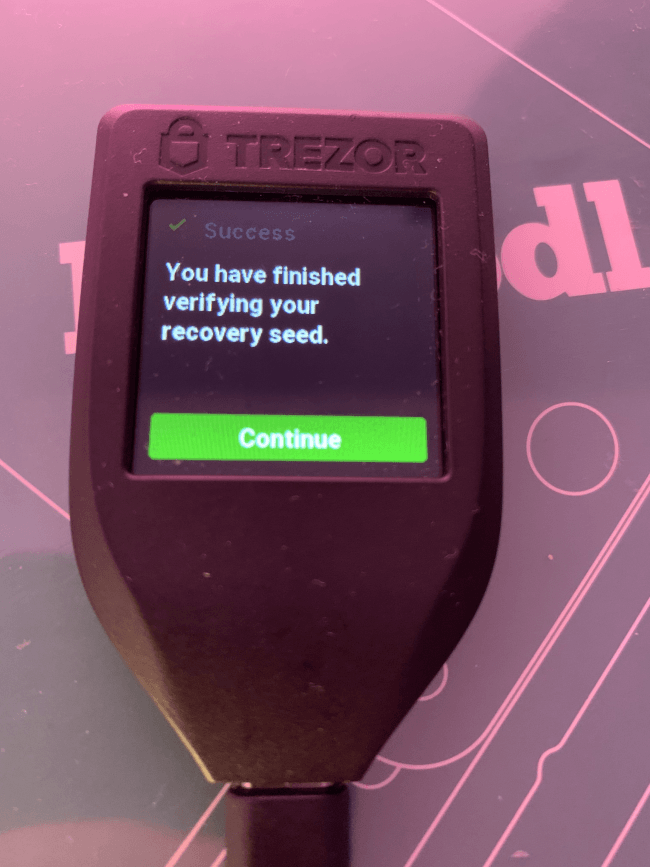
Congratulations, you have set up your Trezor hardware wallet with Electrum! Now you go back to your computer screen and do the last fine tunings. You will have to pick the type of addresses in your wallet. You can’t go wrong with p2sh-segwit, but you can also go native segwit. Legacy addresses are the conservative choice, but picking them will make you pay higher transaction fees. Using the Lightning Network also requires SegWit, so it’s better to support it in one of the two ways.
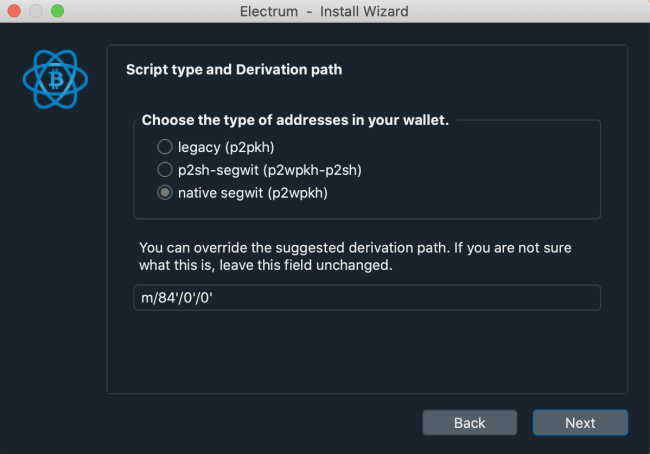
Finally, you can choose to encrypt your wallet. This means that a special file gets saved on your hard drive, and it’s better to put it in cold storage. An external flash drive or SD card will suffice, granted that you do at least 2 of them for redundancy. Also, enabling encryption means that you won’t be able to use your wallet in Electrum without connecting the Trezor first.
From now on, you should be extra careful with your privacy. After taking all these steps, it would be a pity to compromise everything by connecting to centralized servers. So you should avoid using your hardware wallet with Trezor’s online wallet.
If you must install firmware updates, wipe your device and create a new wallet to connect to Trezor. You should master the art of juggling with your wallets and recovering them.
Also, it’s always a good idea to verify your setup with a recovery. But make sure you type your 24 words on your Trezor, as opposed to your computer keyboard. This protects you against malware and all sorts of infections.
COMPARISON
3. Run Trezor on Wasabi Wallet
Wasabi is another popular desktop wallet which is compatible with Trezors. It is not as feature-packed as Electrum, and it has no support for Shamir backups. By default, it can only create basic 12-word seed phrases.
Yet it’s excellent for beginners who want privacy by default. Wasabi has Tor integration, downloads block filters to minimize reliance on third party nodes, and also connects to your own full node. If you have a full node running in the background on the same computer, Wasabi will connect to it. This means that your IP address and UTXO are only saved on your node, which is ideal for privacy.
Info: Like Electrum, Wasabi wallet is available on Windows, Mac, and Linux. Also, Wasabi is best known for its simple CoinJoin feature. Unfortunately, it is not available for hardware wallets. So to do CoinJoins, you will have to move your funds to a hot wallet in Wasabi.
But now let’s talk about what Wasabi can do to maximize your Trezor’s privacy. When you open the wallet, pick the “Hardware Wallet” menu on your left. Connect your Trezor and you will notice that it gets detected. If it doesn’t, click “Search Hardware Wallets” to refresh the search.
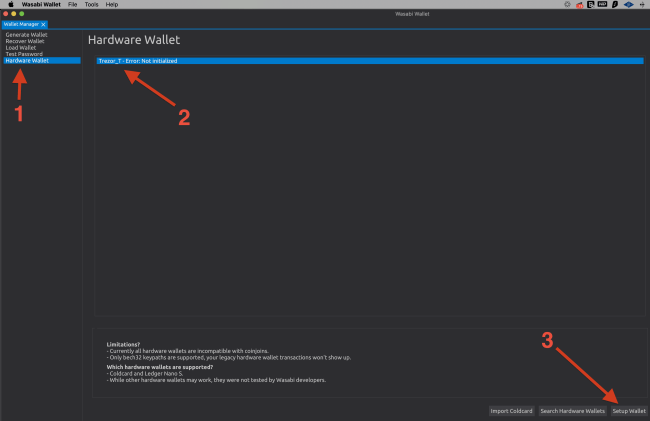
After you select the device, click the “Setup Wallet” button on the bottom right corner. From this point on, all the action moves to the screen of your Trezor hardware wallet. You will have to type your PIN (if you set one), agree with the Terms of Service, and back up your 12 words. The steps are identical with the ones you have in your Electrum wallet setup.
Once you’re done, click “Search Hardware Wallets” once again, select your Trezor and load it. In a few seconds you will see a screen which has 3 tabs: send, receive, and history. Congratulations, you have set up your Trezor hardware wallet on Wasabi! This will help you maintain a higher degree of privacy.
For simplicity purposes, you can also recover your Electrum wallet setup. This means that you use Electrum to generate your private key and then switch to Wasabi for everyday use. The main advantage is that Wasabi runs Tor by default and connects to your full node. The biggest disadvantage is that you complicate your setup. Also, you won’t be able to recover Shamir backups in Wasabi.
Advice: Just like Electrum, Wasabi can't connect to Trezor to install firmware updates. So to complete this process, you must use a disposable setup that you can share with Trezor. And after the update, you wipe the device and back up your Electrum/Wasabi wallet.
This shortcoming can be overcome by running your own instance of the Trezor client. But it requires command line mastery and a basic understanding of Python. It unlocks all the advanced features, but it’s not friendly with newbies at all. So if you’re going to experiment with it, use this guide and generate a wallet that has no coins on it.
Likewise, it’s recommended to use this tutorial and experiment yourself with empty wallets. Once you understand what’s going on and you master the interfaces, you’re ready to also move coins. But until then, use this tutorial as a learning experience. The author and Privacy Pros are not responsible for any losses of funds. So play safe and know why you’re using each tool.
FAQ
What is IP address?
IP address stands for ‘internet protocol address’ and it is written as a string of numbers separated by periods.
What is a public key?
A public key consists in a large numerical value which is used for data encryption. Sofware programs can generate public keys.
Can’t I just store my coins on my exchange?
You can, but it is not recommended. Storing your coins on an exchange can lead to a loss of your coins. Just see what happened to Mt. Gox. It is better to keep your coins on a wallet that you own (meaning only you have the private key of) and then back it up using a Billfodl.
How does a VPN protect me ?
When you connect to a VPN(virtual private network), you are putting an extra server between yourself and the website you want to go to. This server changes your IP address and encrypts your browsing activity.
Can Bitcoin transactions be tracked ?
Unless somebody links your identity with a wallet address you used, your Bitcoin transactions will be anonymous.
Is Trezor Model T safe?
If a very motivated and highly skilled attacker were to physically get hold of your Trezor Model T, your coins may not be safe. However, this attack has never been performed outside of a laboratory, so the threat is remote. In almost all cases, a Trezor Model T will keep your coins very safe.







